Azure Files ベンチマーク
モチベーション
既に公開ドキュメントに記載されていて、新鮮味に欠けるところですが、特にレイテンシについて計ってみたいという目的でベンチマークを取ってみました。[1]
| 使用パターンの要件 | Standard | Premium |
|---|---|---|
| 書き込み待機時間 (1桁のミリ秒) | はい | はい |
| 読み取り待機時間 (1桁のミリ秒) | いいえ | はい |
使用する fio ジョブファイル
fio[2] は、ストレージのベンチマークツールとして良く用いられています。
実際のアクセスパターンに近いベンチマークなど、様々なオプションが用意されています。
また、Windows 向けのバイナリも提供されています。
今回は、fio の Latency profile[3] にあるジョブファイルを使用します。
[global]
bs=4k
random_generator=lfsr
direct=1
ioengine=libaio
iodepth=64
# Set max acceptable latency to 10msec
latency_target=10ms
# profile over a 5s window
latency_window=5s
# 99.9% of IOs must be below the target
latency_percentile=99.9
size=128m
# switch directory option for different mount points
directory=/mnt/testfs
#directory=/mount/saifl7ipbrcon3yprem/testfs
[read]
rw=randread
[write]
rw=randwrite
実施結果
fio
Azure Files (Standard)
結果、レイテンシ lat (msec) を見ると、読み取り (read) / 書き込み (write) 共に一桁ミリ秒でした。
同一リージョンで行っているので、ほぼほぼ Files サービスの待機時間と言っても良いと思います。
[azureuser@linuxvm ~]$ fio ./latency-profile.fio
read: (g=0): rw=randread, bs=(R) 4096B-4096B, (W) 4096B-4096B, (T) 4096B-4096B, ioengine=libaio, iodepth=64
write: (g=0): rw=randwrite, bs=(R) 4096B-4096B, (W) 4096B-4096B, (T) 4096B-4096B, ioengine=libaio, iodepth=64
fio-3.27
Starting 2 processes
read: Laying out IO file (1 file / 128MiB)
write: Laying out IO file (1 file / 128MiB)
Jobs: 2 (f=2): [r(1),w(1)][100.0%][r=1004KiB/s,w=924KiB/s][r=251,w=231 IOPS][eta 00m:00s]
read: (groupid=0, jobs=1): err= 0: pid=51096: Tue Nov 7 02:47:06 2023
read: IOPS=224, BW=897KiB/s (919kB/s)(128MiB/146090msec)
slat (usec): min=10, max=38798, avg=39.81, stdev=214.89
clat (usec): min=2418, max=75258, avg=4412.72, stdev=2766.54
lat (usec): min=2458, max=75343, avg=4453.09, stdev=2774.22
clat percentiles (usec):
| 1.00th=[ 2638], 5.00th=[ 2868], 10.00th=[ 3163], 20.00th=[ 3556],
| 30.00th=[ 3720], 40.00th=[ 3851], 50.00th=[ 3982], 60.00th=[ 4146],
| 70.00th=[ 4359], 80.00th=[ 4752], 90.00th=[ 5342], 95.00th=[ 5932],
| 99.00th=[15401], 99.50th=[21365], 99.90th=[43779], 99.95th=[54789],
| 99.99th=[69731]
bw ( KiB/s): min= 336, max= 1048, per=99.98%, avg=897.57, stdev=114.69, samples=291
iops : min= 84, max= 262, avg=224.39, stdev=28.67, samples=291
lat (msec) : 4=50.54%, 10=47.68%, 20=1.17%, 50=0.53%, 100=0.07%
cpu : usr=0.31%, sys=1.03%, ctx=32871, majf=0, minf=10
IO depths : 1=100.0%, 2=0.0%, 4=0.0%, 8=0.0%, 16=0.0%, 32=0.0%, >=64=0.0%
submit : 0=0.0%, 4=100.0%, 8=0.0%, 16=0.0%, 32=0.0%, 64=0.0%, >=64=0.0%
complete : 0=0.0%, 4=100.0%, 8=0.0%, 16=0.0%, 32=0.0%, 64=0.0%, >=64=0.0%
issued rwts: total=32768,0,0,0 short=0,0,0,0 dropped=0,0,0,0
latency : target=10000000, window=5000000, percentile=99.90%, depth=1
write: (groupid=0, jobs=1): err= 0: pid=51097: Tue Nov 7 02:47:06 2023
write: IOPS=223, BW=895KiB/s (916kB/s)(128MiB/146491msec); 0 zone resets
slat (usec): min=25, max=38908, avg=63.03, stdev=216.04
clat (usec): min=3330, max=38894, avg=4401.21, stdev=1303.11
lat (usec): min=3379, max=43021, avg=4464.82, stdev=1320.42
clat percentiles (usec):
| 1.00th=[ 3523], 5.00th=[ 3654], 10.00th=[ 3720], 20.00th=[ 3818],
| 30.00th=[ 3916], 40.00th=[ 3982], 50.00th=[ 4080], 60.00th=[ 4228],
| 70.00th=[ 4359], 80.00th=[ 4686], 90.00th=[ 5342], 95.00th=[ 5800],
| 99.00th=[ 9110], 99.50th=[12125], 99.90th=[24249], 99.95th=[25822],
| 99.99th=[31327]
bw ( KiB/s): min= 728, max= 984, per=100.00%, avg=895.37, stdev=47.46, samples=292
iops : min= 182, max= 246, avg=223.84, stdev=11.86, samples=292
lat (msec) : 4=41.16%, 10=57.99%, 20=0.72%, 50=0.13%
cpu : usr=0.30%, sys=1.58%, ctx=33054, majf=0, minf=9
IO depths : 1=100.0%, 2=0.0%, 4=0.0%, 8=0.0%, 16=0.0%, 32=0.0%, >=64=0.0%
submit : 0=0.0%, 4=100.0%, 8=0.0%, 16=0.0%, 32=0.0%, 64=0.0%, >=64=0.0%
complete : 0=0.0%, 4=100.0%, 8=0.0%, 16=0.0%, 32=0.0%, 64=0.0%, >=64=0.0%
issued rwts: total=0,32768,0,0 short=0,0,0,0 dropped=0,0,0,0
latency : target=10000000, window=5000000, percentile=99.90%, depth=1
Run status group 0 (all jobs):
READ: bw=897KiB/s (919kB/s), 897KiB/s-897KiB/s (919kB/s-919kB/s), io=128MiB (134MB), run=146090-146090msec
WRITE: bw=895KiB/s (916kB/s), 895KiB/s-895KiB/s (916kB/s-916kB/s), io=128MiB (134MB), run=146491-146491msec
[azureuser@linuxvm ~]$
Azure Files (Premium)
Premium も読み取り/書き込み操作共に、一桁ミリ秒で、 Standard よりも低いレイテンシが得られています。
[azureuser@linuxvm ~]$ fio ./latency-profile.fio
read: (g=0): rw=randread, bs=(R) 4096B-4096B, (W) 4096B-4096B, (T) 4096B-4096B, ioengine=libaio, iodepth=64
write: (g=0): rw=randwrite, bs=(R) 4096B-4096B, (W) 4096B-4096B, (T) 4096B-4096B, ioengine=libaio, iodepth=64
fio-3.27
Starting 2 processes
read: Laying out IO file (1 file / 128MiB)
write: Laying out IO file (1 file / 128MiB)
Jobs: 1 (f=1): [_(1),w(1)][100.0%][w=1269KiB/s][w=317 IOPS][eta 00m:00s]
read: (groupid=0, jobs=1): err= 0: pid=51191: Tue Nov 7 02:53:14 2023
read: IOPS=335, BW=1343KiB/s (1375kB/s)(6716KiB/5001msec)
slat (nsec): min=8700, max=94301, avg=19137.39, stdev=4943.26
clat (usec): min=1732, max=13041, avg=2954.31, stdev=543.75
lat (usec): min=1753, max=13060, avg=2973.89, stdev=543.72
clat percentiles (usec):
| 1.00th=[ 1909], 5.00th=[ 2114], 10.00th=[ 2311], 20.00th=[ 2507],
| 30.00th=[ 2737], 40.00th=[ 2900], 50.00th=[ 3032], 60.00th=[ 3130],
| 70.00th=[ 3195], 80.00th=[ 3294], 90.00th=[ 3359], 95.00th=[ 3490],
| 99.00th=[ 4178], 99.50th=[ 5538], 99.90th=[ 7308], 99.95th=[13042],
| 99.99th=[13042]
bw ( KiB/s): min= 1304, max= 1370, per=100.00%, avg=1343.20, stdev=25.11, samples=10
iops : min= 326, max= 342, avg=335.60, stdev= 6.31, samples=10
lat (msec) : 2=2.50%, 4=96.13%, 10=1.31%, 20=0.06%
cpu : usr=0.30%, sys=0.88%, ctx=1684, majf=0, minf=54
IO depths : 1=100.0%, 2=0.0%, 4=0.0%, 8=0.0%, 16=0.0%, 32=0.0%, >=64=0.0%
submit : 0=0.0%, 4=100.0%, 8=0.0%, 16=0.0%, 32=0.0%, 64=0.0%, >=64=0.0%
complete : 0=0.0%, 4=100.0%, 8=0.0%, 16=0.0%, 32=0.0%, 64=0.0%, >=64=0.0%
issued rwts: total=1679,0,0,0 short=0,0,0,0 dropped=0,0,0,0
latency : target=10000000, window=5000000, percentile=99.90%, depth=1
write: (groupid=0, jobs=1): err= 0: pid=51192: Tue Nov 7 02:53:14 2023
write: IOPS=326, BW=1307KiB/s (1338kB/s)(128MiB/100277msec); 0 zone resets
slat (usec): min=4, max=113, avg=19.43, stdev= 8.02
clat (usec): min=2203, max=33007, avg=3036.16, stdev=883.33
lat (usec): min=2220, max=33016, avg=3056.03, stdev=883.74
clat percentiles (usec):
| 1.00th=[ 2376], 5.00th=[ 2507], 10.00th=[ 2606], 20.00th=[ 2769],
| 30.00th=[ 2835], 40.00th=[ 2900], 50.00th=[ 2966], 60.00th=[ 2999],
| 70.00th=[ 3064], 80.00th=[ 3130], 90.00th=[ 3294], 95.00th=[ 3490],
| 99.00th=[ 5407], 99.50th=[ 8717], 99.90th=[15008], 99.95th=[15795],
| 99.99th=[26084]
bw ( KiB/s): min= 1168, max= 1376, per=99.99%, avg=1307.76, stdev=41.26, samples=200
iops : min= 292, max= 344, avg=326.88, stdev=10.31, samples=200
lat (msec) : 4=97.59%, 10=1.99%, 20=0.39%, 50=0.03%
cpu : usr=0.35%, sys=0.83%, ctx=32819, majf=0, minf=9
IO depths : 1=100.0%, 2=0.0%, 4=0.0%, 8=0.0%, 16=0.0%, 32=0.0%, >=64=0.0%
submit : 0=0.0%, 4=100.0%, 8=0.0%, 16=0.0%, 32=0.0%, 64=0.0%, >=64=0.0%
complete : 0=0.0%, 4=100.0%, 8=0.0%, 16=0.0%, 32=0.0%, 64=0.0%, >=64=0.0%
issued rwts: total=0,32768,0,0 short=0,0,0,0 dropped=0,0,0,0
latency : target=10000000, window=5000000, percentile=99.90%, depth=1
Run status group 0 (all jobs):
READ: bw=1343KiB/s (1375kB/s), 1343KiB/s-1343KiB/s (1375kB/s-1375kB/s), io=6716KiB (6877kB), run=5001-5001msec
WRITE: bw=1307KiB/s (1338kB/s), 1307KiB/s-1307KiB/s (1338kB/s-1338kB/s), io=128MiB (134MB), run=100277-100277msec
[azureuser@linuxvm ~]$
ioping
簡易的にストレージのベンチマークが取れる ioping でも計測してみました。
まずは、ioping のインストール。
$ sudo dnf install git gcc -y
$ git clone https://github.com/koct9i/ioping.git
$ cd ioping/
$ make ioping
ioping の結果では、Standard の方が良い結果が得られてしまっていますが、
簡易的なベンチマークとしては利用する分には良さそうです。
Azure Files (Standard)
[azureuser@linuxvm ioping]$ ./ioping -c 5 -D /mnt/testfs
4 KiB <<< /mnt/testfs (cifs //saifl7ipbrcon3y.file.core.windows.net/testfs 5 TiB): request=1 time=3.69 ms (warmup)
4 KiB <<< /mnt/testfs (cifs //saifl7ipbrcon3y.file.core.windows.net/testfs 5 TiB): request=2 time=4.30 ms
4 KiB <<< /mnt/testfs (cifs //saifl7ipbrcon3y.file.core.windows.net/testfs 5 TiB): request=3 time=4.96 ms
4 KiB <<< /mnt/testfs (cifs //saifl7ipbrcon3y.file.core.windows.net/testfs 5 TiB): request=4 time=3.80 ms
4 KiB <<< /mnt/testfs (cifs //saifl7ipbrcon3y.file.core.windows.net/testfs 5 TiB): request=5 time=4.04 ms
--- /mnt/testfs (cifs //saifl7ipbrcon3y.file.core.windows.net/testfs 5 TiB) ioping statistics ---
4 requests completed in 17.1 ms, 16 KiB read, 233 iops, 935.5 KiB/s
generated 5 requests in 4.00 s, 20 KiB, 1 iops, 4.99 KiB/s
min/avg/max/mdev = 3.80 ms / 4.28 ms / 4.96 ms / 431.3 us
Azure Files (Premium)
[azureuser@linuxvm ioping]$ ./ioping -c 5 -D /mount/saifl7ipbrcon3yprem/testfs
4 KiB <<< /mount/saifl7ipbrcon3yprem/testfs (nfs4 saifl7ipbrcon3yprem.file.core.windows.net:/saifl7ipbrcon3yprem/testfs 100 GiB): request=1 time=5.79 ms (warmup)
4 KiB <<< /mount/saifl7ipbrcon3yprem/testfs (nfs4 saifl7ipbrcon3yprem.file.core.windows.net:/saifl7ipbrcon3yprem/testfs 100 GiB): request=2 time=5.74 ms
4 KiB <<< /mount/saifl7ipbrcon3yprem/testfs (nfs4 saifl7ipbrcon3yprem.file.core.windows.net:/saifl7ipbrcon3yprem/testfs 100 GiB): request=3 time=6.29 ms
4 KiB <<< /mount/saifl7ipbrcon3yprem/testfs (nfs4 saifl7ipbrcon3yprem.file.core.windows.net:/saifl7ipbrcon3yprem/testfs 100 GiB): request=4 time=6.51 ms
4 KiB <<< /mount/saifl7ipbrcon3yprem/testfs (nfs4 saifl7ipbrcon3yprem.file.core.windows.net:/saifl7ipbrcon3yprem/testfs 100 GiB): request=5 time=4.71 ms
--- /mount/saifl7ipbrcon3yprem/testfs (nfs4 saifl7ipbrcon3yprem.file.core.windows.net:/saifl7ipbrcon3yprem/testfs 100 GiB) ioping statistics ---
4 requests completed in 23.2 ms, 16 KiB read, 172 iops, 688.2 KiB/s
generated 5 requests in 4.00 s, 20 KiB, 1 iops, 4.99 KiB/s
min/avg/max/mdev = 4.71 ms / 5.81 ms / 6.51 ms / 697.5 us
環境構築
環境構築は、Azure Bicep で行いました。
参考までにこちらに載せておきます。
各リソースの構築は、モジュールで呼び出す形になっています。
.
├── linuxfileshare.bicep
└── modules
├── filesnfs.bicep
├── filessmb.bicep
├── installpkg.txt
├── linuxvm.bicep
└── vnet.bicep
- linuxfileshare.bicep
var sshpubkey = loadTextContent('../.ssh/id_rsa.pub')
module deployvnet './modules/vnet.bicep' = {
name: 'vnet'
params: {
addressPrefix: '10.1.0.0/16'
virtualNetworkName: 'vnet'
subnetName: 'default'
subnetAddressPrefix: '10.1.0.0/24'
}
}
module deployvm './modules/linuxvm.bicep' = {
name: 'vm'
params: {
adminPasswordOrKey: '${sshpubkey}'
virtualNetworkName: 'vnet'
subnetName: 'default'
}
dependsOn: [
deployvnet
]
}
module deploysmbsshare './modules/filessmb.bicep' = {
name: 'smbshare'
params: {
enableLargeFileShare: 'Disabled'
}
}
module deploynfsshare './modules/filesnfs.bicep' = {
name: 'nfsshare'
params: {
subnetName: 'default'
virtualNetworkName: 'vnet'
}
dependsOn: [
deployvnet
]
}
- modules/vnet.bicep
@description('Location')
param location string = resourceGroup().location
@description('Name of the virtual network')
param virtualNetworkName string
@description('Address prefix of vnet')
param addressPrefix string
@description('Name of the subnet')
param subnetName string
@description('Address prefix of subnet')
param subnetAddressPrefix string
@description('Name of the NSG')
param networkSecurityGroupName string = 'nsg'
resource networkSecurityGroup 'Microsoft.Network/networkSecurityGroups@2023-04-01' = {
name: networkSecurityGroupName
location: location
properties: {
securityRules: [
{
name: 'AllowSSH'
properties: {
protocol: 'Tcp'
sourcePortRange: '*'
destinationPortRange: '22'
sourceAddressPrefix: '*'
destinationAddressPrefix: '*'
access: 'Allow'
priority: 1000
direction: 'Inbound'
}
}
]
}
}
resource virtualNetwork 'Microsoft.Network/virtualNetworks@2023-05-01' = {
name: virtualNetworkName
location: location
properties: {
addressSpace: {
addressPrefixes: [
addressPrefix
]
}
}
}
resource subnet 'Microsoft.Network/virtualNetworks/subnets@2023-04-01' = {
parent: virtualNetwork
name: subnetName
properties: {
addressPrefix: subnetAddressPrefix
networkSecurityGroup: {
id: networkSecurityGroup.id
}
}
}
- modules/linuxvm.bicep
トラステッド起動に関するパラメータやコメントアウト箇所は使用していません。
@description('Virtual Machine Name')
param vmName string = 'linuxvm'
@description('Username for VM')
param adminUsername string = 'azureuser'
@description('Type of authentication to user on the VM.')
@allowed(['password', 'sshPublicKey'])
param authenticationType string = 'sshPublicKey'
@description('SSH Public Key to use for authentication')
@secure()
param adminPasswordOrKey string
@description('The Suse version for VM.')
@allowed(['sles-12-sp5', 'sles-15-sp5', 'RHEL-92-lvm', 'RHEL-88'])
param osVersion string = 'RHEL-92-lvm'
@description('Location for all resources.')
param location string = resourceGroup().location
@description('Size of VM')
param vmSize string = 'Standard_D16s_v4'
@description('Name of the virtual network')
param virtualNetworkName string
@description('Name of subnet')
param subnetName string
@description('Security Type of the VM')
@allowed(['Standard', 'TrustedLaunch'])
param securityType string = 'Standard'
var imageReference = {
'sles-15-sp5': {
publisher: 'SUSE'
offer: 'sles-15-sp5'
sku: 'gen2'
version: 'latest'
}
'sles-12-sp5': {
publisher: 'SUSE'
offer: 'sles-12-sp5'
sku: 'gen2'
version: 'latest'
}
'RHEL-88': {
publisher: 'RedHat'
offer: 'RHEL'
sku: '8_8'
version: 'latest'
}
'RHEL-92-lvm': {
publisher: 'RedHat'
offer: 'RHEL'
sku: '9-lvm'
version: 'latest'
}
}
var publicIPAddressName = '${vmName}-pip'
var networkInterfaceName = '${vmName}-nic'
var osDiskType = 'Standard_LRS'
var linuxConfiguration = {
disablePasswordAuthentication: true
ssh: {
publicKeys: [
{
path: '/home/${adminUsername}/.ssh/authorized_keys'
keyData: adminPasswordOrKey
}
]
}
}
var securityProfile = {
uefiSettings: {
secureBootEnabled: true
vTPMEnabled: true
}
securityType: securityType
}
// for cloud-init custom data
var cloudInit = base64(loadTextContent('./installpkg.txt'))
var extensionName = 'GuestAttestation'
var extensionPublisher = 'Microsoft.Azure.Security.LinuxAttestation'
var extensionVersion = '1.0'
var maaTenantName = 'GuestAttestation'
var maaEndpoint = substring('emptystring', 0, 0)
resource virtualNetwork 'Microsoft.Network/virtualNetworks@2023-05-01' existing = {
name: virtualNetworkName
}
resource subnet 'Microsoft.Network/virtualNetworks/subnets@2023-05-01' existing = {
parent: virtualNetwork
name: subnetName
}
resource publicIPAddress 'Microsoft.Network/publicIPAddresses@2023-04-01' = {
name: publicIPAddressName
location: location
sku: {
name: 'Basic'
}
properties: {
publicIPAllocationMethod: 'Dynamic'
publicIPAddressVersion: 'IPv4'
idleTimeoutInMinutes: 4
}
}
resource networkInterface 'Microsoft.Network/networkInterfaces@2023-04-01' = {
name: networkInterfaceName
location: location
properties: {
ipConfigurations: [
{
name: 'ipconfig1'
properties: {
privateIPAllocationMethod: 'Dynamic'
subnet: {
id: subnet.id
}
publicIPAddress: {
id: publicIPAddress.id
}
}
}
]
}
}
resource premdiskv1 'Microsoft.Compute/disks@2023-04-02' = {
name: 'premdiskv1'
location: location
properties: {
creationData: {
createOption: 'Empty'
}
diskSizeGB: 64
}
sku: {
name: 'Premium_LRS'
}
}
resource vm 'Microsoft.Compute/virtualMachines@2023-03-01' = {
name: vmName
location: location
properties: {
hardwareProfile: {
vmSize: vmSize
}
storageProfile: {
osDisk: {
createOption: 'FromImage'
managedDisk: {
storageAccountType: osDiskType
}
}
dataDisks: [
{
createOption: 'Attach'
managedDisk: {
id: premdiskv1.id
}
lun: 0
}
]
imageReference: imageReference[osVersion]
}
networkProfile: {
networkInterfaces: [
{
id: networkInterface.id
}
]
}
osProfile: {
computerName: vmName
adminUsername: adminUsername
adminPassword: adminPasswordOrKey
linuxConfiguration: ((authenticationType == 'password') ? null : linuxConfiguration)
customData: cloudInit
}
securityProfile: ((securityType == 'Standard') ? null : securityProfile)
diagnosticsProfile: {
bootDiagnostics: {
enabled: true
}
}
}
}
/*
resource vmExtension 'Microsoft.Compute/virtualMachines/extensions@2023-03-01' = {
parent: vm
name: extensionName
location: location
properties: {
publisher: extensionPublisher
type: extensionName
typeHandlerVersion: extensionVersion
autoUpgradeMinorVersion: true
enableAutomaticUpgrade: true
settings: {
AttestationConfig: {
MaaSettings: {
maaEndpoint: maaEndpoint
maaTenantName: maaTenantName
}
}
}
}
}
*/
- modules/installpkg.txt
#cloud-config
package_upgrade: true
packages:
- fio
- cifs-utils
- nfs-utils
- modules/filessmb.bicep
@description('Location')
param location string = 'japaneast'
@description('File Share Name')
param fileShareName string = 'testfs'
@description('Storage account name')
param storageAccountName string = 'sa${uniqueString(resourceGroup().id)}'
@description('Storage Account Sku')
@allowed([
'Standard_LRS', 'Standard_GRS', 'Standard_RAGRS', 'Standard_ZRS', 'Premium_LRS'
])
param storageAccountSku string = 'Standard_LRS'
@description('Enable LargeFileShare option')
@allowed(['Disabled', 'Enabled'])
param enableLargeFileShare string
resource storageAccount 'Microsoft.Storage/storageAccounts@2021-04-01' = {
name: storageAccountName
location: location
kind: 'StorageV2'
sku: {
name: storageAccountSku
}
properties: {
largeFileSharesState: enableLargeFileShare
}
resource fileService 'fileServices' existing = {
name: 'default'
}
}
resource fileshare 'Microsoft.Storage/storageAccounts/fileServices/shares@2021-04-01' = {
parent: storageAccount::fileService
name: fileShareName
properties: {
enabledProtocols: 'SMB'
}
}
- modules/filesnfs.bicep
@description('Location')
param location string = resourceGroup().location
@description('Name of the virtual network')
param virtualNetworkName string
@description('Name of subnet')
param subnetName string
@description('File Share Name')
param fileShareName string = 'testfs'
@description('Storage account name')
param storageAccountName string = 'sa${uniqueString(resourceGroup().id)}prem'
@description('Storage Account Sku')
@allowed([
'Premium_LRS', 'Premium_ZRS'
])
param storageAccountSku string = 'Premium_LRS'
@description('Root Squash Configurtion')
param rootSquash string = 'NoRootSquash'
var filePrivateDnsZoneName = 'privatelink.file.core.windows.net'
resource virtualNetwork 'Microsoft.Network/virtualNetworks@2023-05-01' existing = {
name: virtualNetworkName
}
resource subnet 'Microsoft.Network/virtualNetworks/subnets@2023-05-01' existing = {
parent: virtualNetwork
name: subnetName
}
resource storageAccount 'Microsoft.Storage/storageAccounts@2021-04-01' = {
name: storageAccountName
location: location
kind: 'FileStorage'
sku: {
name: storageAccountSku
}
properties: {
supportsHttpsTrafficOnly: false
}
resource fileService 'fileServices' existing = {
name: 'default'
}
}
resource fileshare 'Microsoft.Storage/storageAccounts/fileServices/shares@2021-04-01' = {
parent: storageAccount::fileService
name: fileShareName
properties: {
enabledProtocols: 'NFS'
rootSquash: rootSquash
}
}
resource filesharePE 'Microsoft.Network/privateEndpoints@2023-05-01' = {
name: '${fileShareName}-pe'
location: location
properties: {
subnet: {
id: subnet.id
}
privateLinkServiceConnections: [
{
name: '${fileShareName}-plsc'
properties: {
privateLinkServiceId: storageAccount.id
groupIds: [
'file'
]
}
}
]
}
dependsOn: [
fileshare
]
}
resource filePDZ 'Microsoft.Network/privateDnsZones@2020-06-01' = {
name: filePrivateDnsZoneName
location: 'global'
properties: {
}
}
resource filePDZLink 'Microsoft.Network/privateDnsZones/virtualNetworkLinks@2020-06-01' = {
parent: filePDZ
name: '${fileShareName}-pdzlink'
location: 'global'
properties: {
registrationEnabled: false
virtualNetwork: {
id: virtualNetwork.id
}
}
}
resource filePDZG 'Microsoft.Network/privateEndpoints/privateDnsZoneGroups@2023-05-01' = {
parent: filesharePE
name: '${fileShareName}-pdzg'
location: location
properties: {
privateDnsZoneConfigs: [
{
name: 'dnsConfig'
properties: {
privateDnsZoneId: filePDZ.id
}
}
]
}
}
上記の Bicep ファイルを使用して、以下のコマンドで環境を構築します。
$ az group create -n labperf -l japaneast
$ az deployment group create -g labperf --template-file ./azure-bicep/linuxfileshare.bicep
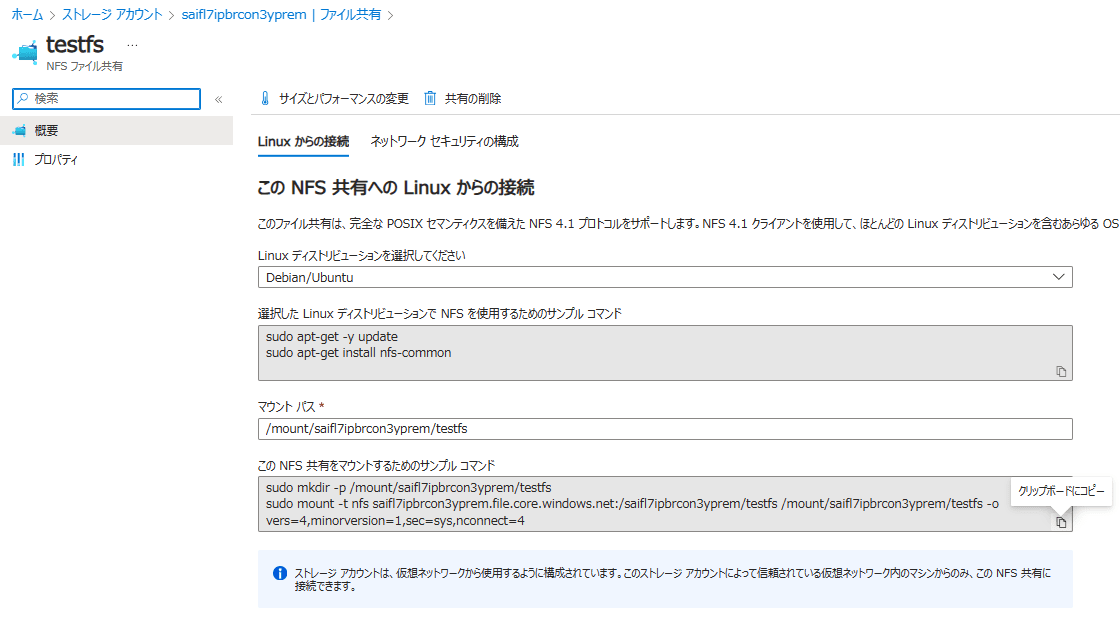
完了後、仮想マシン (linuxvm) に SSH 接続して、
各ファイル共有をマウントします。

[azureuser@linuxvm ~]$ df -h
Filesystem Size Used Avail Use% Mounted on
...(省略)...
//saifl7ipbrcon3y.file.core.windows.net/testfs 5.0T 384M 5.0T 1% /mnt/testfs
saifl7ipbrcon3yprem.file.core.windows.net:/saifl7ipbrcon3yprem/testfs 100G 0 100G 0% /mount/saifl7ipbrcon3yprem/testfs
これで、Azure Files (Standard/Premium) がマウントできました。
Discussion